Identity is behind 80% of today’s attacks, and access brokers are growing 112%. This article explains why it matters.
Introduction
Backups Don’t Equal Recovery
Most organizations believe they’re prepared for a cyber incident because they have backups.
But when ransomware strikes, that assumption is often the first thing that breaks.
That’s not fear-mongering. That’s the reality most enterprises are walking into – often without realizing it.
True cyber recovery isn’t about whether data exists somewhere.
It’s about whether you can restore cleanly, quickly, and with confidence – under pressure.
In ransomware recovery scenarios, enterprises repeatedly discover the same hard truth: backups alone don’t guarantee recovery. Corrupted data, compromised credentials, slow restoration, and unclear ownership turn technical incidents into business crises.
Downtime isn’t just an IT inconvenience. It’s revenue loss, regulatory exposure, reputational damage, and operational paralysis.
This is why cyber recovery has become a core pillar of every modern cyber resilience strategy, not an afterthought.
Click here to book your free assessment – limited slots available
Forward-thinking organizations are now reimagining how their global capability centre operates-shifting toward smarter, outcome-driven delivery models supported by IT MSP providers that enable faster execution, stronger governance, and sustained cost efficiency. Global Capability Center – Cloud Tech Services
80% of cyberattacks start with identity abuse.
Scroll to see how organizations shut the front door – fast. Backups Don’t Equal Recovery
Table of Contents
Why Backups Fail When It Matters Most
After a cyberattack, organizations expect recovery to be straightforward. In reality, data recovery after cyber attack is where complexity peaks.
Here’s why backups often fall short:
- Backup environments are accessed using the same compromised credentials
- Malware remains dormant inside backup copies
- Recovery timelines stretch from hours into days or weeks
- Restoration procedures were never tested at scale
- Teams don’t know which version of data is clean and safe
This is the uncomfortable answer to why backups fail during ransomware attacks:
They were never designed for adversarial recovery – only for accidental loss.
Traditional backup strategies were built to recover deleted files or failed systems. They were not engineered to defend against attackers actively trying to corrupt recovery paths.
And threat actors know this.
With a 112% surge in access broker activity, attackers are scaling faster than enterprise recovery models are evolving.
Cyber Recovery Requires More Than Storage
A resilient enterprise doesn’t just store data – it engineers recovery.
An effective cyber resilience strategy focuses on:
- Isolation of clean data copies
- Immutable recovery environments
- Identity-secured access during incidents
- Orchestrated recovery workflows
- Regular validation and testing
This is where cyber recovery shifts from an IT task to a business capability.
Executives don’t ask if data exists. They ask when operations resume.
And that answer depends on whether recovery has been tested under real-world conditions – not just documented in a policy.
How to Ensure Data Recovery After Ransomware
So, how to ensure data recovery after ransomware?
Enterprises that recover fastest share a few common traits:
- Recovery environments are isolated from production and attack paths
- Access controls are hardened specifically for recovery scenarios
- Clean data copies are verified, not assumed
- Recovery processes are rehearsed, not improvised
- Ownership is clearly defined across IT, security, and operations
From Capability to Confidence: Cyber Recovery in Practice
This is where we purpose-built cyber recovery solutions become essential.
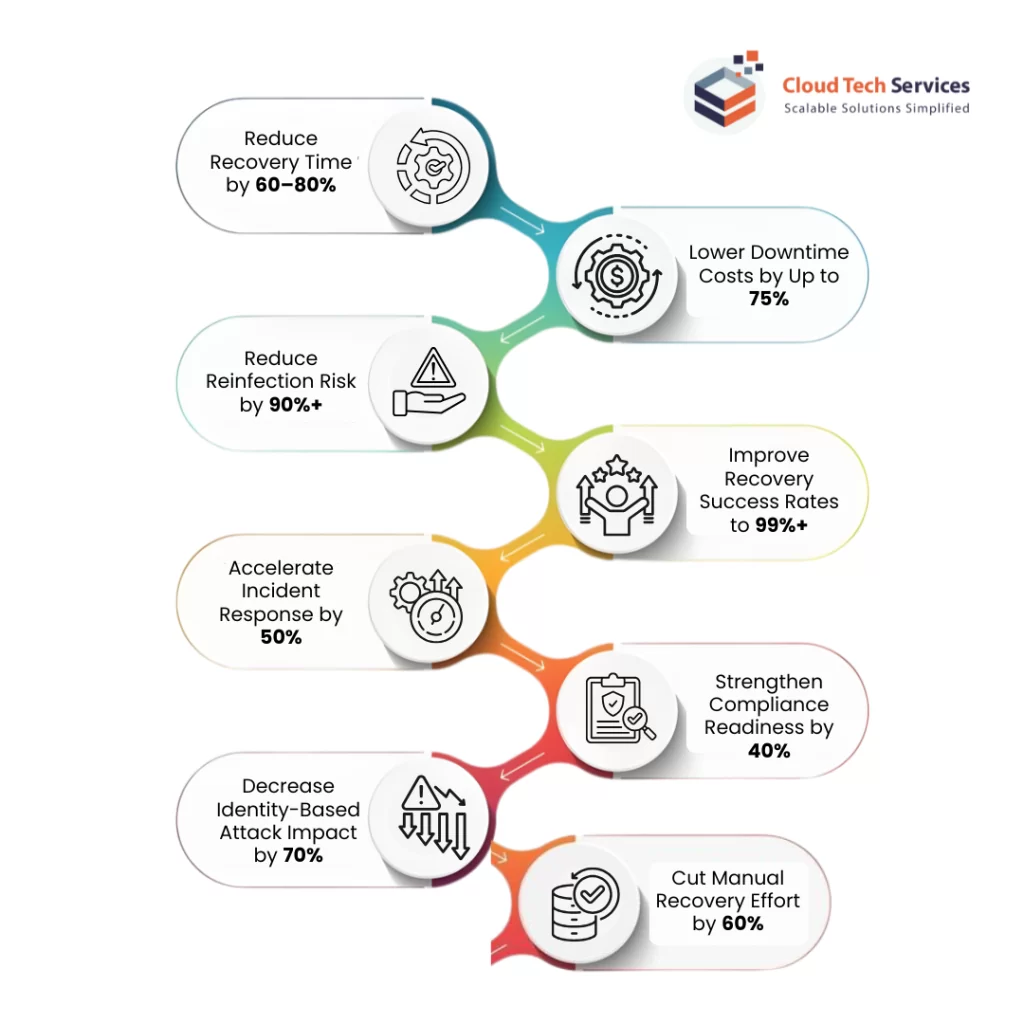
Modern platforms and services are designed to:
- Restore data without reintroducing malware
- Reduce recovery time objectives (RTOs) dramatically
- Maintain compliance during recovery
- Support forensic investigation alongside restoration
For large organizations, recovery must work across hybrid, cloud, and legacy environments – without slowing the business.
Enterprise environments are rarely simple. They span multiple clouds, on-prem data centers, SaaS platforms, and complex identity ecosystems. Recovery must operate seamlessly across all of them.
If restoration works in one environment but fails in another, the business still stops.
That’s why cyber recovery services for enterprises must be engineered for scale, coordination, and repeatability – not one-off incident handling.
Why Enterprises Turn to Specialized Ransomware Recovery Services
As attacks grow more sophisticated, many organizations rely on ransomware recovery services to reduce risk and uncertainty.
These services bring:
- Proven recovery playbooks
- Skilled incident-response and recovery specialists
- Tested recovery environments
- Clear accountability during high-pressure events
For enterprises, this isn’t outsourcing – it’s risk management.
Internal teams are already stretched across modernization, compliance, and operational initiatives. During an active incident, clarity and execution speed matter more than ever.
Specialized cyber recovery services for enterprises ensure recovery ownership doesn’t fragment when pressure rises.
Conclusion: Confidence Is the Real Measure of Cyber Recovery
Cyber recovery isn’t proven when backups exist – it’s proven when your business can restore fast, completely, and under pressure.
In today’s ransomware landscape, uncertainty is the biggest risk.
Organizations that test recovery, validate integrity, and align recovery to business priorities don’t just survive attacks – they resume operations with confidence.
If you don’t know how quickly you can restore, what you can restore, or whether your data is clean, your recovery strategy is incomplete.
Backups are necessary.
But they are not enough.